5 Unconventional Knowledge About data center audit That You Can't Learn From Books.
Checklist aids smooth information centre shift adjustments
INFINITI is a 1-quit information centre options provider with an eye for detail and outstanding buyer service. With decades of experience, IT Operations Managers and Engineers return to us time right after time, due to our higher levels of experience, efficiency, and information. We cater to all elements of mission critical IT environments with goods and a service that is second to none.
For that reason, there is definitely no truth to the statement that ANSI/TIA-942 hinders innovation when designing information centres. With 2015 underway, program normal preventive maintenance with this checklist as a guide to access prospective problems affecting your information center cooling environment. Check if their standards match what the AICPA and other organizations set out. Amanaged security service provider that tends to make an effort to comply with government regulations is far more probably to offer top quality information protection.

Computers and other equipment employed for the information center are exempt from property taxes under Iowa law, for these data centers that meet the above specifications. This could mean millions of dollars in savings for larger businesses that have much more gear. The data center wants to be in a location exactly where it is secure from all-natural disasters such as hurricanes, earthquakes, tsunamis and floods. Any facility should be constructed outdoors of a 500-year flood plain location to steer clear of flooding. Man-made issues such as the prospective for terrorist attacks also want to be regarded.
Information Safety Checklist To Boost Victim Security & Privacy Web page 1 of two Information safety involves a variety of issues An outdoors Safety Audit can provide an in-depth evaluation of what is weak or missing. So there are various actions to take into account when developing and implementing a security policy for datacentres. Creating and utilizing successful controls is all about breaking down the troubles into basic parts and employing focused remediations, rather than trying to locate an overarching remedy. Some of these methods could be regarded overkill for a modest firm, with a reasonably modest datacentre needing protection, but the capability to handle who has access to the comms space or datacentre need to never ever be overlooked. The subsequent category of controls is physical safety controls, which have a tendency to be extremely visible from outside a datacentre, and act as a deterrent to opportunistic thieves.
This course is the very first and only complete course to cover the SEED requirements. Participants will learn the detailed technical requirements and their scoring criteria. The course contains sufficient examples and practical sharing that the participants are capable to apply them proper away in their facilities.
Pundit Data Center Consulting Group has emerged as a industry leader for 21st century information center approaches, management, evaluations and functionality. So, coming back to the query of “Outcome primarily based or checklist or can it be each? †UTI is outcome based and does not give sensible guidance on how to achieve it. ANSI/TIA-942 is also outcome based but provides guidance by means of clear descriptions in numerous annexes and a supplemental table for you to use. These with much more advanced technical expertise can nonetheless use the flexibility to implement the design and style differently as extended as they meet the outcome objectives and guidance of the annexes.
All the practices are applicable to each in-property and colocation data centres. No matter how basic or complicated the safety program, it needs to be tested regularly to guarantee it performs as anticipated. Most data centers have some level of compliance and certification such as Uptime Institute, Tier III and ISO27001. When IT executives talk about safety, it frequently revolves around defense against cyber attacks employing clever technologies. Nevertheless, cyber security is just part of the equation physical security - keeping the poor guys from physically accessing servers - is also crucial.
What is a DCIM tool?
A telecom data center is a facility owned and operated by a Telecommunications or Service Provider company such as BT, AT&T or Verizon. These types of data centers require very high connectivity and are mainly responsible for driving content delivery, mobile services, and cloud services.
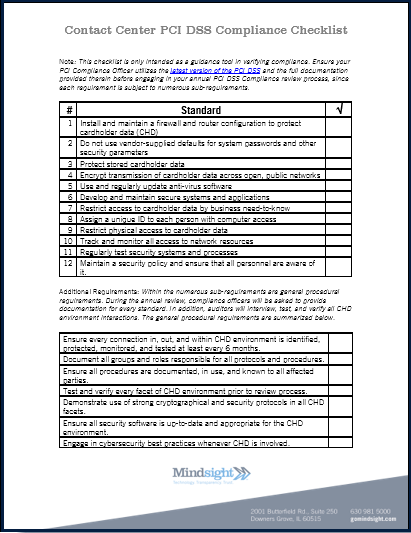
Their platforms and services turn into essential components of their clients’ operations and have to supply sophisticated security. By following the pace of alter in the industry, PCI remains a relevant common for all e-commerce companies. PCI DSS was developed by the PCI SSC (Payment Card Market Security Standards Council), whose members included credit card organizations such as Visa, Mastercard, American Express, and so on. The key concept behind their collaborative effort to create this normal was to aid improve the safety of customers’ financial details. HIPAA (Wellness Insurance coverage Portability and Accountability Act) regulates data, Cloud storage safety, and management best practices in the healthcare market.
Assure network safety policy, decrease security risk, and attain continuous compliance. Learners are also necessary to bring a webcam enabled laptop or suitable device with unrestricted wireless net connectivity, the newest web browser and appropriate applications for reading/annotating PDFs and editing normal office documents. Knowledge of functioning inside a information centre atmosphere is essential preferably with two years encounter in a technical IT or facilities part.
- DNV GL Business Assurance is one of the top providers of accredited management systems certification.
- The CMSO outputs can be identified in GitHub , even though common information and activities are obtainable from the CMSO website .
- The normal specifies requirements fordata centersincluding single tenant enterprise data centers and multi-tenant Net hosting data centers.
- The IT industry has changed drastically with on the internet access to stored information necessary 24/7.
- The firm is the 1st in Europe and a single of only two (the other becoming in the US) global colocation data centres operating with OCP on pilot programmes for validation.
Men and women have the proper to view all the private information held by an organisation on them. If make contact with records are decentralised and spread across a range of equipment, then accumulating this data will prove a challenge. The Common Data Protection Regulation (GDPR), effective as of 25th Might 2018, will influence nearly every business. It has been introduced in the UK through a new information protection bill, making companies far more accountable for the safety of private data.
To support you make a more informed decision about your data center services, right here is an overview of concepts you must understand. The correct challenge is that several outdoors of the auditing realm could not fully comprehend the different classifications. They may possibly not even know what to look for in a information center style and certification. Securing your data center or selecting a compliant provider should be the core of your safety method. Let an data centre to be far more competitive in front of the sustainability-conscious buyers.
Offered the sensitive nature of healthcare information, any institution that handles them must stick to strict safety practices. HIPAA and PCI DSS are two critical notions to recognize when evaluating data center security. The computer relocations important purpose of SOC 1 is to give data about a service provider’s manage structure. It is especially critical for SaaS and technology companies that provide some essential solutions to organizations. In that respect, they are far more integrated into their clients’ processes than a general business partner or collaborator would be.

If you would like to talk about your experience or suitability for this system please contact us. A certified CDCAP® also considers the requirements for compliance, having a full understanding of national and international regulations, codes and standards. During the system, learners will be supplied a worthwhile opportunity to access the newest industry requirements.
What are the different types of data centers?
· Definition of Modern Data Center (MDC); the characteristics of MDC - modernized infrastructure, automating services, and transforming people and processes. · Modernized IT infrastructure technologies: Converged, Flash, Scale out, Software-defined, Cloud-enabled, Protected, and Trusted.
Of the reports relevant to data centers, SOC 1 is the closest to the old SAS 70. The service organization (data center) defines internal controls against which audits are performed. Nevertheless, it’s crucial to realize that there is no certification for SSAE 16. It is a common created by the Auditing Requirements Board (ASB) of the American Institute of Certified Public Accountants (AICPA). data center cabling design A lengthy-time standard all through the information center market, SAS 70 was officially retired at the end of 2010.
The enterprise implications
In a much less populated region, there is reduce threat simply because it is significantly less most likely to take place. When it comes to data center location, providers need to take into account geographic stability. To guarantee your data environment is secure, a information center colocation provider must be positioned in a threat-free atmosphere. The following essential locations of the data center among others ought to be tested in specifics by the Auditor to assure of manage effectiveness server relocation services and adequacy and ought to be part of the Auditors’ Audit Plan/Checklist for Data Center. If you opt to wipe storage by software program, then confident that it meets standards necessary by your industry and data sensitivity.